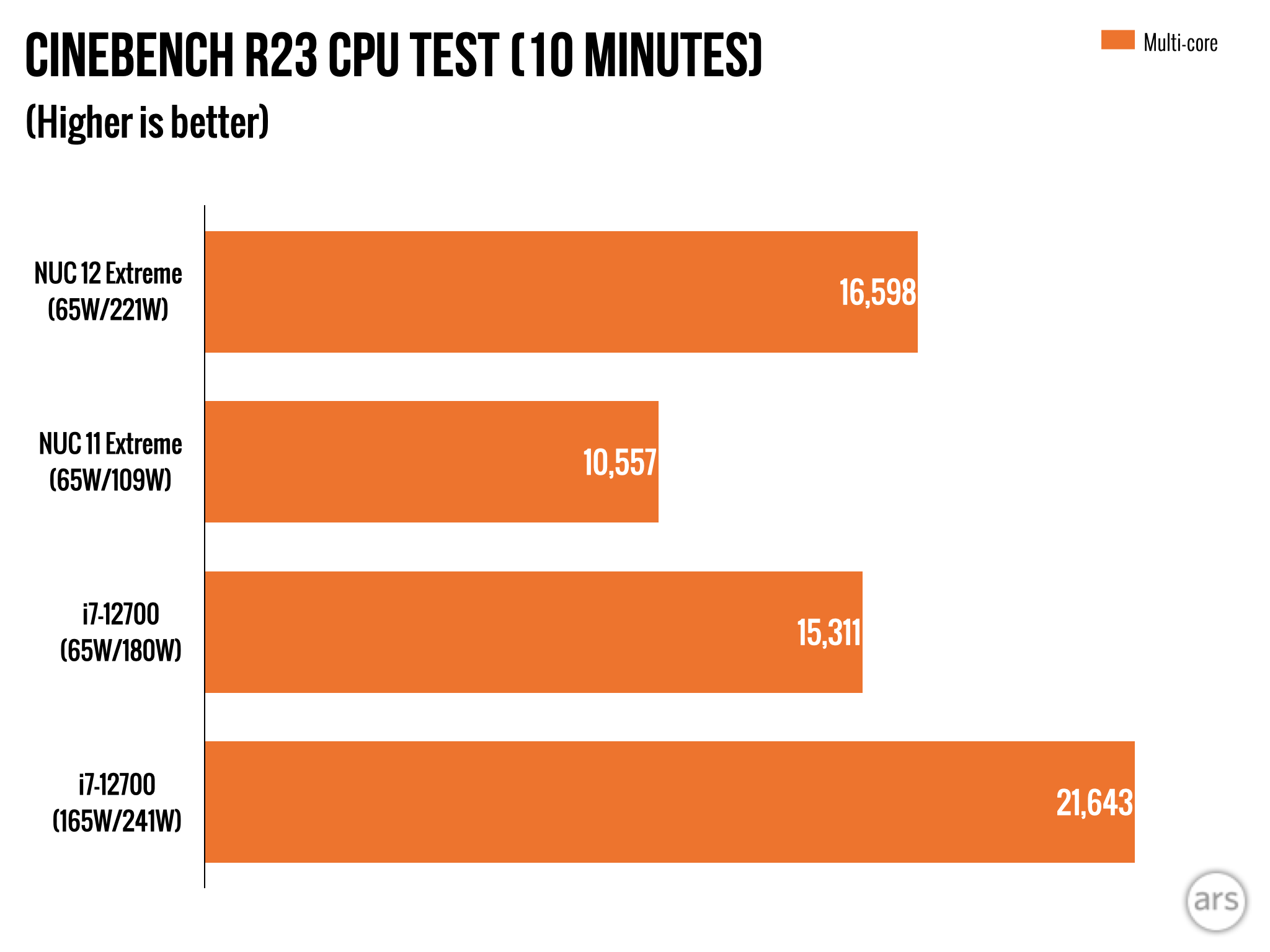
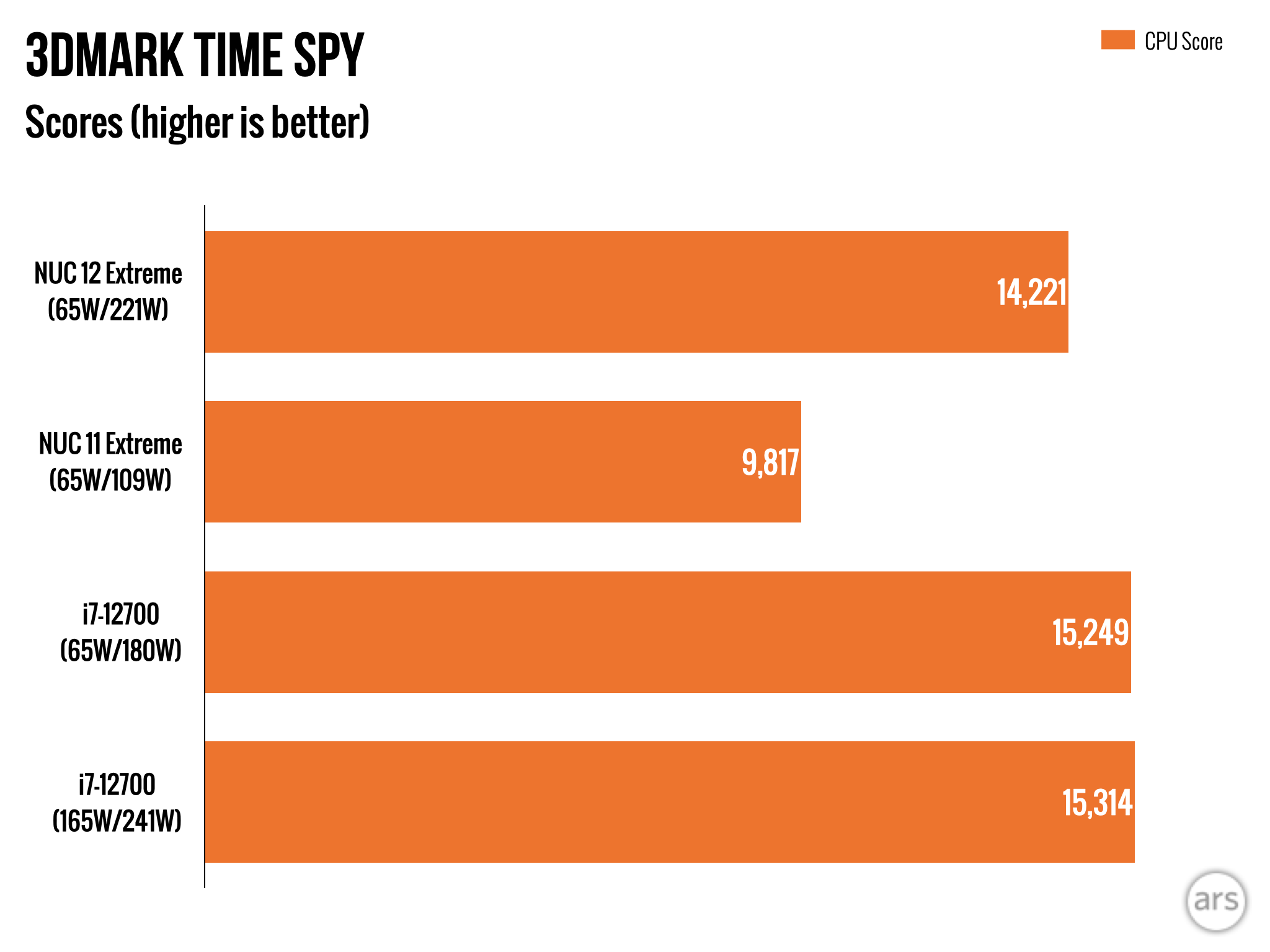
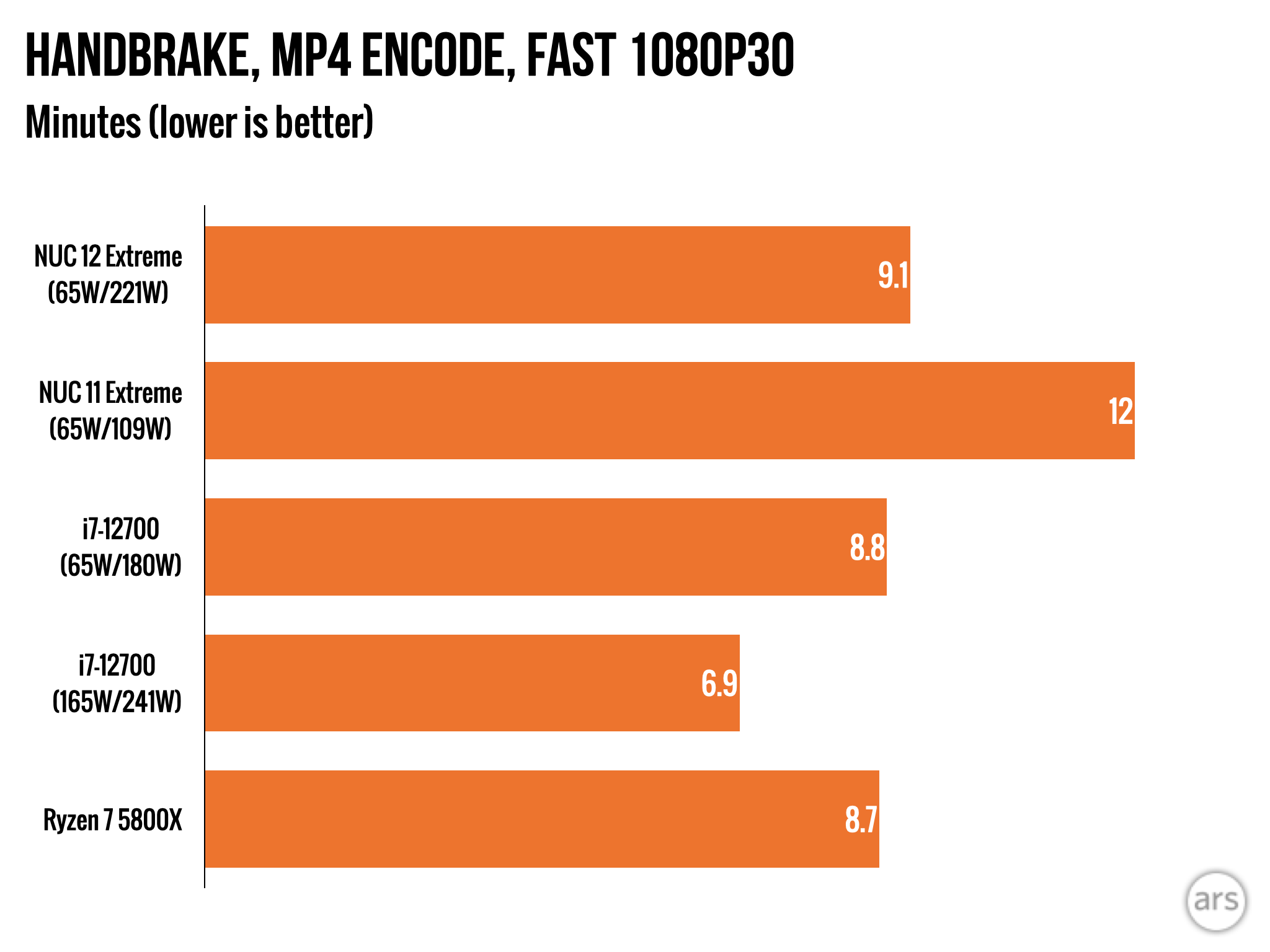
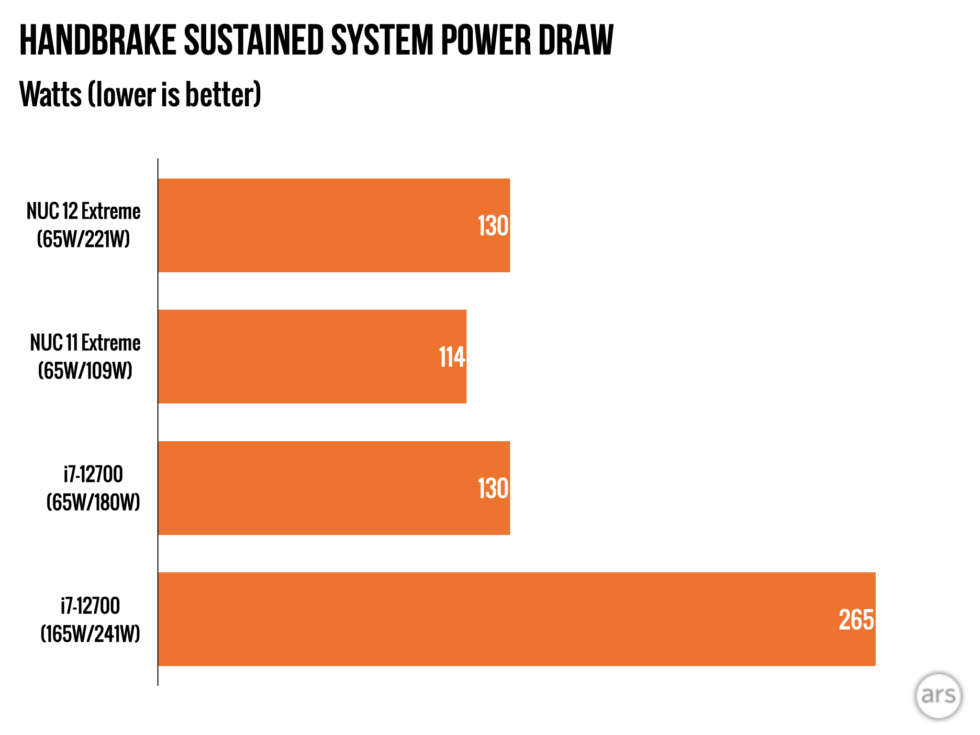
Much of the spyware you hear of today are the powerful nation-state-backed exploits that can quietly and remotely hack into iPhones anywhere in the world. These powerful hacking tools are bought and operated by governments, often targeting their most vocal critics — journalists, activists and human rights defenders.
There is another kind of spyware that is more prevalent and much more likely to affect the average person: the consumer-grade spyware apps that are controlled by everyday people.
Consumer-grade spyware is often sold under the guise of child monitoring software, but also goes by the term “stalkerware” for its ability to track and monitor other people or spouses without their consent. Stalkerware apps are installed surreptitiously by someone with physical access to a person’s phone and are hidden from home screens, but will silently and continually upload call records, text messages, photos, browsing history, precise location data and call recordings from the phone without the owner’s knowledge. Many of these spyware apps are built for Android, since it’s easier to plant a malicious app than on iPhones, which have tighter restrictions on what kind of apps can be installed and what data can be accessed.
Last October, TechCrunch revealed a consumer-grade spyware security issue that’s putting the private phone data, messages and locations of hundreds of thousands of people, including Americans, at risk.
But in this case it’s not just one spyware app exposing people’s phone data. It’s an entire fleet of Android spyware apps that share the same security vulnerability.
TechCrunch first discovered the vulnerability as part of a wider exploration of consumer-grade spyware. The vulnerability is simple, which is what makes it so damaging, allowing near-unfettered remote access to a device’s data. But efforts to privately disclose the security flaw to prevent it from being misused by nefarious actors has been met with silence both from those behind the operation and from Codero, the web company that hosts the spyware operation’s back-end server infrastructure.
The nature of spyware means those targeted likely have no idea that their phone is compromised. With no expectation that the vulnerability will be fixed any time soon, TechCrunch is now revealing more about the spyware apps and the operation so that owners of compromised devices can uninstall the spyware themselves, if it’s safe to do so.
Given the complexities in notifying victims, CERT/CC, the vulnerability disclosure center at Carnegie Mellon University’s Software Engineering Institute, has also published a note about the spyware.
What follows are the findings of a months-long investigation into a massive stalkerware operation that is harvesting the data from some 400,000 phones around the world, with the number of victims growing daily, including in the United States, Brazil, Indonesia, India, Jamaica, the Philippines, South Africa and Russia.
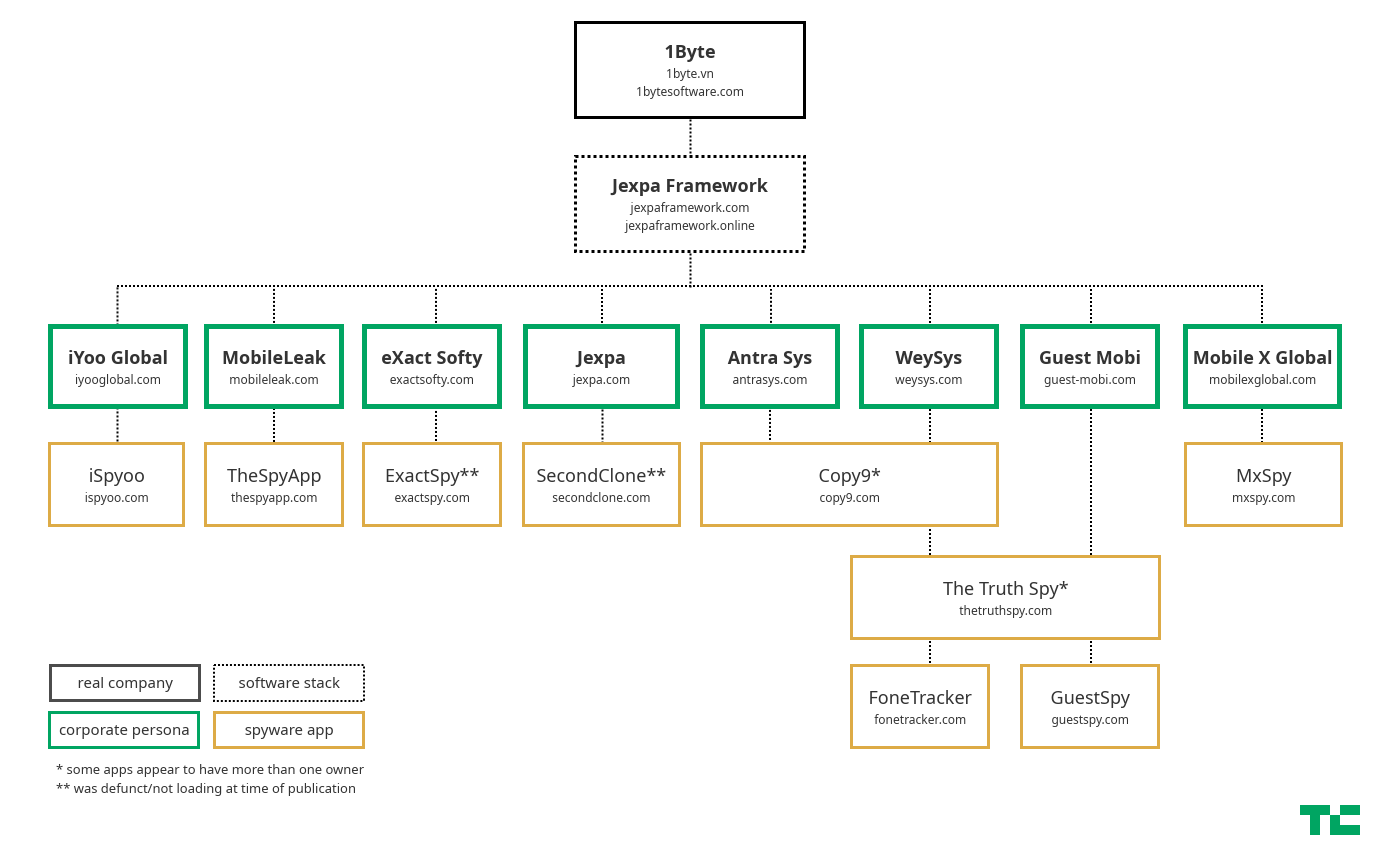
On the front line of the operation is a collection of white-label Android spyware apps that continuously collect the contents of a person’s phone, each with custom branding, and fronted by identical websites with U.S. corporate personas that offer cover by obfuscating links to its true operator. Behind the apps is a server infrastructure controlled by the operator, which is known to TechCrunch as a Vietnam-based company called 1Byte.
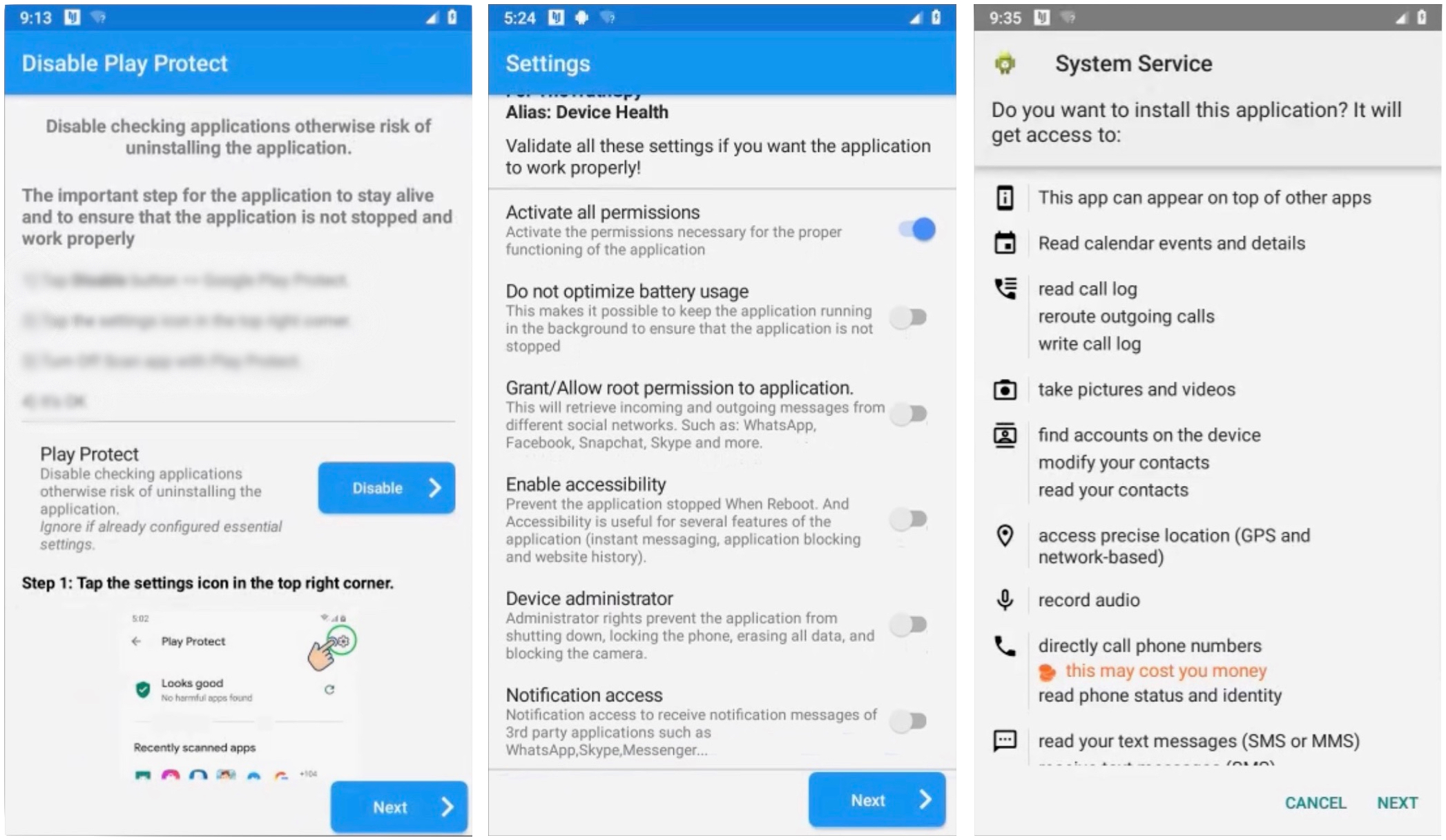
The user interface for planting the spyware. Image Credits: TechCrunch
TechCrunch found nine nearly identical spyware apps that presented with distinctly different branding, some with more obscure names than others: Copy9, MxSpy, TheTruthSpy, iSpyoo, SecondClone, TheSpyApp, ExactSpy, FoneTracker and GuestSpy.
Other than their names, the spyware apps have practically identical features under the hood, and even the same user interface for setting up the spyware. Once installed, each app allows the person who planted the spyware access to a web dashboard for viewing the victim’s phone data in real time — their messages, contacts, location, photos and more. Much like the apps, each dashboard is a clone of the same web software. And, when TechCrunch analyzed the apps’ network traffic, we found the apps all contact the same server infrastructure.
But because the nine apps share the same code, web dashboards and the same infrastructure, they also share the same vulnerability.
The vulnerability in question is known as an insecure direct object reference, or IDOR, a class of bug that exposes files or data on a server because of sub-par, or no, security controls in place. It’s similar to needing a key to unlock your mailbox, but that key can also unlock every other mailbox in your neighborhood. IDORs are one of the most common kinds of vulnerability; TechCrunch has found and privately disclosed similar flaws before, such as when LabCorp exposed thousands of lab test results, and the recent case of CDC-approved health app Docket exposing COVID-19 digital vaccine records. IDORs have an advantage in that they can often be fixed at the server level without needing to roll out a software update to an app, or in this case a fleet of apps.
But shoddy coding didn’t just expose the private phone data of ordinary people. The entire spyware infrastructure is riddled with bugs that reveal more details about the operation itself. It’s how we came to learn that data on some 400,000 devices — though perhaps more — have been compromised by the operation. Shoddy coding also led to the exposure of personal information about its affiliates who bring in new paying customers, information that they presumably expected to be private; even the operators themselves.
A web of companies that don’t seem to exist
Behind each branded app, web dashboard and front-facing website is what appears to be a fictitious parent company with its own corporate website. The parent company websites are visually identical and all claim to be “software outsourcing” companies with over a decade of experience and hundreds of engineers, with each website claiming one of the nine branded apps as their flagship product.
If the identical websites weren’t an immediate red flag, the parent company websites are all hosted on the same web server. TechCrunch also searched state and public databases but found no current business records exist for any of the purported parent companies.
One of the many parent companies is Jexpa. Like the rest of the parent companies, Jexpa does not appear to exist on paper, but for a time an entity by that name did. Jexpa was registered as a technology company in California in 2003, but was suspended from the state’s business registry in 2009. The company’s domain was abandoned and left to expire.
Jexpa’s expired domain was purchased by an undisclosed buyer in 2015. (TechCrunch has found no evidence of any connection between the former Jexpa and the 2015 purchaser of Jexpa.com.) Jexpa.com now purports to be the site of a software outsourcing company, but is packed with stock photos and dummy pages and uses the likeness of several real-world identities, like “Leo DiCaprio,” but using the photo of Brazilian director Fernando Meirelles. The operators have gone to considerable lengths to conceal their true involvement in the operation, including registering email addresses using the identities of other people — in one case using the name and photo of a NYPD deputy commissioner and a former shipping executive in another.
The structure of the spyware apps and company personas set up by 1Byte. Image Credits: TechCrunch
But Jexpa runs deeper than just a name. TechCrunch found several overlaps between Jexpa and the branded spyware apps, including a set of release notes that was likely not meant to be public but had been left behind — and exposed — on its servers.
The release notes contain about three years of detailed changes and fixes to the back-end web dashboards, describing how the spyware has evolved since the log was first created in late-2018, with its most recent fixes deployed in April 2021. The notes were signed by a developer with a Jexpa.com email address.
The notes also describe fixes to what the developers call the Jexpa Framework, the software stack running on its servers that it uses to host the operation, each brand’s web dashboard and the storage for the massive amounts of phone data collected from the spyware apps themselves. We know this because, just as they had done with the release notes, the developers also left their technical documentation and the source code for the Jexpa Framework exposed to the internet.
The documentation laid out specific technical configurations and detailed instructions, with poorly redacted screenshots that revealed portions of several domains and subdomains used by the spyware apps. Those same screenshots also exposed the operator’s own website, but more on that in a moment. The documentation pages also use examples of the spyware apps themselves, like SecondClone, and meticulously describe how to set up new content storage servers for each app from scratch, even down to which web host to use — such as Codero, Hostwinds and Alibaba — because they allow for a particular disk storage setup required for the apps to work.
For a company with no apparent business filings, the operator put considerable effort into making Jexpa look like the top of the operation. But the operator left behind a trail of internet records, exposed source code and documentation that connects Jexpa, the Jexpa Framework and the fleet of spyware apps to a Vietnam-based company called 1Byte.
A short time after we contacted 1Byte about the vulnerability and its links to Jexpa, the Jexpa Framework’s documentation pages were put behind a password wall, shutting us out.
From London to Vietnam
1Byte looks like any other software startup, a small team of Android and .NET developers living and working just outside of Vietnam’s capital Ho Chi Minh City. Its Facebook page shows the group at team outings, dinners and enjoying the rewards of their work. But 1Byte is the same group of developers behind this enormous spyware operation that facilitates the surveillance of hundreds of thousands of people around the world.
The layers that they built to distance themselves from the operation suggests the group may be aware of the legal, or at least the reputational, risks associated with running an operation of this kind.
It’s not only 1Byte that’s apparently keen to keep its involvement a secret. The affiliates, who help to sell the software, also made efforts to conceal their identities.
1Byte set up another company called Affiligate, which handles the payments for new customers buying the spyware and also gets the affiliates paid. Affiligate was set up under the guise of allowing app developers to sell their software, but in reality it is a small marketplace that sells mostly spyware. But shoddy coding seems to follow 1Byte wherever it goes. A bug in Affiligate’s marketplace is leaking the real identities of affiliates in the browser every time the page loads.
Affiligate presents itself as a company based either in the U.K. or France, depending on where on its website you look. It even lists 1Byte as its Singapore office, though TechCrunch has found no evidence that 1Byte has any physical presence in Singapore. Public records show a U.K. company was incorporated under the name Affiligate in 2019 to Daniel Knights and later struck-off by the U.K. registrar in March 2021. Efforts by TechCrunch to locate and reach Daniel Knights were unsuccessful.
Only one other name shows up in Affiligate’s paperwork. The U.K. registrar records showed Affiligate’s only shareholder is Van Thieu, whose address on the paperwork puts him at a virtual office space in London. Thieu’s profile on LinkedIn lists him as a 1Byte shareholder in Vietnam, and in his profile photo he can be seen wearing a T-shirt with the 1Byte logo. Thieu is also the director of 1Byte, and is believed to be the head of the spyware operation. Though he is not listed on its website, Thieu is seen in several team photos on the group’s Facebook page. TechCrunch has identified two other 1Byte employees through the Affiligate bug, and another employee who left their name in the Jexpa Framework’s code.
TechCrunch emailed 1Byte with details of the security vulnerability. The emails were opened, according to our email open tracker, but we did not get a reply. We followed up with 1Byte using the email address we had previously messaged, but the email bounced and was returned with an error message stating that the email address no longer exists. Emails sent directly to 1Byte employees were delivered but we did not receive any replies.
Since contacting 1Byte and known affiliates, at least two of the branded spyware apps appeared to cease working or shut down.
READ MORE ON TECHCRUNCH
That leaves us here. Without a fix, or intervention from the web host, TechCrunch cannot disclose more about the security vulnerability — even if it’s the result of bad actors themselves — because of the risk it poses to the hundreds of thousands of people whose phones have been unknowingly compromised by this spyware.
We have put together an explainer on how to remove the spyware from your phone, if you believe it is safe to do so. Because spyware is covert-by-design, keep in mind that removing the spyware will likely alert the person who planted it, which could create an unsafe situation. You can find support and resources on how to create a safety plan from the Coalition Against Stalkerware and the National Network to End Domestic Violence.
Despite the growing threat posed by consumer-grade spyware in recent years, U.S. authorities have been hamstrung by legal and technical challenges in their efforts to tackle spyware operations.
Stalkerware still operates in a gray space in the United States, since the possession of spyware itself is not illegal. Federal prosecutors have in rare cases taken action against those who illegally plant spyware used for the sole purpose of surreptitiously intercepting a person’s communications in violation of federal wiretapping laws. But the government’s enforcement powers against operators are limited at best, and overseas spyware operators find themselves largely out of the jurisdictional reach of U.S. law enforcement.
Instead, much of the front-line effort against stalkerware has been fought by antivirus makers and cybersecurity companies working together with human rights defenders at the technical level. The Coalition Against Stalkerware launched in 2019 and works to support victims and survivors of stalkerware. The coalition shares resources and samples of known stalkerware so information about new threats can be given to other cybersecurity companies and automatically blocked.
In 2020, Google banned stalkerware apps on the Google Play store, and later blocked stalkerware apps from advertising in its search results, albeit with mixed results.
Where laws have been largely ineffective at curbing spyware, federal authorities have sometimes used novel legal approaches to justify taking civil action against operators, like for failing to adequately protect the vast amounts of phone data that they collect, often by citing U.S. consumer protection and data breach laws. Last year, the Federal Trade Commission banned SpyFone from the surveillance industry in the first order of its kind after its “lack of basic security” led to the public exposure of data on more than 2,000 phones. In 2019, the FTC settled with Retina-X after it was hacked several times, and eventually shut down.
Stalkerware at large is no stranger to security problems; mSpy, Mobistealth, Flexispy, Family Orbit, KidsGuard and pcTattleTale have all made headlines in recent years for spilling, exposing or falling victim to hackers who access vast troves of phone data.
Now an entire fleet of stalkerware apps can be added to the pile.
If you or someone you know needs help, the National Domestic Violence Hotline (1-800-799-7233) provides 24/7 free, confidential support to victims of domestic abuse and violence. If you are in an emergency situation, call 911. The Coalition Against Stalkerware also has resources if you think your phone has been compromised by spyware. You can contact this reporter on Signal and WhatsApp at +1 646-755-8849 or zack.whittaker@techcrunch.com by email.
Adblock test (Why?)
Behind the stalkerware network spilling the private phone data of hundreds of thousands - TechCrunch
Read More