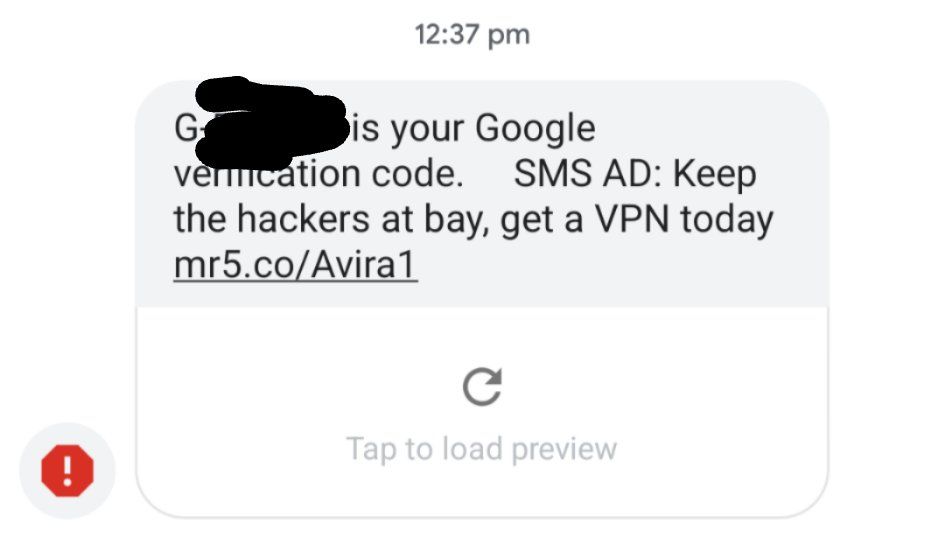
An unidentified carrier in Australia is suspected of injecting advertisements into two-factor SMS messages, according to Chris Lacy, the developer of Action Launcher. The text shows a Google sign-in verification code in the Google Messages app, which funnily enough, even flagged the text as spam.
I just received a two factor authentication SMS from Google that included an ad. Google’s own Messages SMS app flagged it as spam.
What a shameful money grab. pic.twitter.com/NeStIndR6q
— Chris Lacy (@chrismlacy) June 29, 2021
This is possible because SMS messages are unencrypted, and therefore, your carrier can read all of them. Injecting advertisements into 2FA texts ensures that the end-user will actually see the advertisement, as it’s assumed they’ll need to use the code to access whatever service they are trying to log in to. While it’s absolutely a scummy move, it’s made possible because of how poorly protected SMS is. A number of employees from Google have chimed in to say that this is definitely not done by Google and that it’s likely the work of whatever carrier Chris Lacy is using. Mark Risher, Director of Product Management on Identity and User Security at Google, took to Twitter to say that “these are not Google ads and we do not condone this practice.” Furthermore, he says that Google is “working with the wireless carrier to understand why this happened and ensure it doesn’t happen again.”
To close the loop, these are not Google ads and we do not condone this practice. We are working with the wireless carrier to understand why this happened and ensure it doesn’t happen again.
Glad Google Messages flagged it as unsafe 🛑 https://t.co/MqSZgh1uUK
— mark risher (@mrisher) June 29, 2021
While using SMS for two-factor authentication is technically insecure, for most people, it really does not matter. It’s an extra level of security that’s easily accessible and simple to use for most people, and it’s better than nothing. Most people will not be able to conveniently use hardware-based two-factor authentication, which is why SMS-based 2FA is still so widely used. While SIM swap attacks exist, for most people, they aren’t something they will ever need to worry about. If anything, though, it’s impressive that the Google Messages app still managed to pick up that the message was spam, even though it was sent from a Google phone number.
We have reached out to Google for comment as it was their two-factor message that was tampered with, and we will update this article if we get a response. Chris Lacy is electing not to name the carrier “for privacy reasons”, but it’s important to note that this could happen on any carrier if you’re using SMS. Once RCS is widely adopted and end-to-end encryption for text messages becomes the norm, this will no longer be possible as carriers won’t be able to determine which messages contain two-factor codes and which do not.
Carrier suspected of injecting ads into two-factor SMS messages - XDA Developers
Read More
No comments:
Post a Comment